Online interactions go beyond simple communication across the web. It also involves data sharing, sometimes voluntarily and other times involuntarily. That is why veteran internet users prioritize data protection. But why is data privacy important?
When exposed, other internet users can collect your online data, accessing your personal information like your social security details. That is especially possible through social media and when browsing insecure websites. This article helps you to understand the concept of privacy for your online data and how to implement it.

What Is Data Privacy?
Data or online information privacy describes the responsible handling of personal and sensitive information online. Unlike many assert, this concept does not only cover individual’s control of their data. Instead, it concerns how all interacting parties handle personal data, especially its sharing.
You can view this concept as a right and a capacity. For service users, information privacy describes their right to control how their online service providers collect and share their data.
However, at the individual level, the concept describes individuals’ actions and measures to keep their data private. Whatever internet users do to ensure their data remains undisclosed falls under this concept.

Data Protection vs Data Security: Understanding the Difference
Many internet users use data protection and data security interchangeably to mean the same thing. However, they are individual concepts with different meanings. This section will give insight into their meanings and differences.
Data or information protection is the right and ability to control who can access your personal digital information. It also covers the control over what these parties can do with the information they access.
On the other hand, data security describes the protection of digital information from destruction, disruption, modification, and unauthorized access. Therefore, while data security covers its protection, protection entails controlling what those with access can do with the data.
Data security is a much broader term than protection. In fact, information protection relies on data security, but this is not the case for the other way around. To implement data security, you need sophisticated systems, including secure facilities and hardware systems.
Below are five methods employed in implementing data security:
- Access control
- Online activity monitoring
- Breach response
- Network security
- Authentication
Some of these methods may require data encryption, categorization and classification, masking and redaction of data, and automated reporting.

4 Tips for Protecting Data Privacy
The daily increase in data breaches on the internet continues to fuel the debate for and against internet usage. Nevertheless, this digital technology has become part of our lives, one you cannot do without.
So, it is only reasonable to find ways for protecting data privacy while using the internet. This way, you’ll enjoy the benefits of the internet while protecting your information. Therefore, this section will discuss four tips for protecting your information privacy online.
1. Avoid Public Wi-Fi Networks and Use VPNs
Public wifi networks are convenient alternatives for using the internet. Large establishments provide them as complimentary offers for their services to satisfy their customers. Many love using these public wifi networks because they are free, saving them data charges.
However, several risks come with using these public networks. Many of these networks are insecure, allowing hackers to tap into your connection and view your personal information. Remember, several others are on that same network, and that may include a hacker. Moreover, hackers find this an easy way to find susceptible targets.
Instead, using a Virtual Private Network (VPN) to access the internet, even when browsing from home, is best. VPN service allows you to select a server and a location to connect to the internet.
It then encrypts your data from end-to-end, using top-tier encryption protocols like OpenVPN. It also scrambles your data so that even if someone intercepts it, they can’t decipher and use it.
A VPN service will also mask your IP address and assign you another to promote anonymity when using the internet. Thus, with this service, you can rest assured of the privacy and security of your data.

2. Keep Your Personal Information Private
Ignorant of data and privacy protection, many internet users indiscriminately share their personal information online. They’ll readily share their location on social platforms like Twitter, now called X. Some use their personal information to join email lists or fill out surveys to earn bonuses and perks from websites.
True, you may share this information with reputable and trustworthy sources, but a hacker can breach their system. When such cyber threats materialize, hackers may access your personal information. The strength of your online security and your level of privacy depends on you. So, only share your data when you must to intensify your online security.
Also, avoid saving your passwords on your browser. Saving passwords makes it convenient to access your account frequently on your workstation. They also help you access your account freely, even when you forget your password.
However, saving passwords on your browser also comes with risks. If you lose your device for any reason, someone else may gain unrestricted access to your accounts on that device. Even someone you borrow your device to may access your account and personal information from the device.
So, it is good practice to avoid saving passwords on a browser. If you already saved passwords for some accounts, delete them immediately. Instead of saving passwords, use simple but strong passwords and store them else in case you forget.
3. Do Not Open Unfamiliar Links and Attachments
Professional hackers can access your personal information through malware introduced into your device. However, no one would readily accept malware on their device. So, these criminals introduce them through phishing links.
While using your device, you may receive a prompt to click on a link to access mouthwatering offers. That is one popular way hackers advertise phishing links. They also send such links through fake emails with a professional outlook.
Once you click such links, some may introduce malware that allows the hacker to access all your information. Others may lead you to a fake page where they’ll prompt you to provide some personal details.
Always avoid such links to protect your data and keep it private. It also helps to cover your digital footprints while interacting online. Many hackers follow your digital prints to discern what appeals to you and set their bait accordingly.
4. Use Cybersecurity Tools and Products To Protect Your Data
This method is a popular option for businesses and organizations to adopt. Notwithstanding, you can also find versions for individual use among popular security products.
You can purchase and install some of these products on your devices to protect and keep your data private. Some of these products help you detect malware and viruses. Others monitor your connection in real time to fish out breaches and attempts.
The most basic cybersecurity product you get is antivirus software. You can support it with a firewall to provide additional security. You can also add tracking technologies to find who seeks to breach your data.

Understanding Twitter Data Privacy Policies
Like all social platforms, Twitter is an interactive platform. However, to foster interactions and improve users’ experience, the platform collects users’ data and shares some of it. So, what guides this data collection and sharing?
Answering this question will help us understand Twitter’s data privacy policies for all registered users. Remember, information privacy deals with the control of data sharing and usage.
Twitter collects your information to provide you with their service. They also use this information to understand your preferences and modify or improve these services. Regarding sharing, Twitter only shares data you permit them to and with people you authorize them to share it with.
Consider how Twitter complies with information privacy laws while running the platform.
How Twitter Maintains Data Privacy and Compliance With Privacy Laws
Every individual reserves the right to information privacy while using the internet through any medium. Twitter understands this, which is why it implements policies for data privacy and ensures compliance with privacy laws. This section details how the social media giants achieve this legal compliance.
First, Twitter fulfills its legal obligations to publish its privacy policy. This publication allows users to learn how Twitter collects and utilizes their data. Publishing the privacy policies is important for Twitter to uphold the privacy of its users’ information.
The information from Twitter’s privacy policy equips users to control what they share with the platform. Knowing how Twitter collects and shares their data will help them manipulate the process better.
Twitter collects your data in three distinct ways, including:
- The data you provide them. These include your email, account password, card details, preferences, biometric information, etc.
- Data collected automatically as you use the platform. This data comes from your posts, interactions, and communication with Twitter support.
- Data collected from third parties you use with Twitter. That includes device and cookie IDs, email addresses, and other site information.
You can still control data collected automatically when using the platform by modifying your Twitter settings. These settings allow you to choose how much information you share and how much you withhold.

Why Is Data Privacy Important to Twitter?
It is important to Twitter because several users entrust their personal information to its administrators. Thus far, this article has shown the meaning of information privacy and how you can implement it. Now, let’s discuss why this concept is important for social media platforms like Twitter.
Social platforms like X expose users to several audiences. While this exposure primarily promotes social interaction, some individuals join the platform with ulterior intentions.
Now, you already know how detrimental a small privacy breach in data affects an individual. That is why information privacy is important to Twitter. They implement privacy policies to ensure that only what a user allows will reach the public. Twitter remains committed to protecting the private information of all its users.
To ensure data protection and privacy, they employ several data security measures like encryption, authentication, and network security. That is Twitter’s part in promoting your information privacy when using the platform.
After learning why data privacy is important, you can also uphold it by adhering to the platform’s policies. Another way to protect your data is by reducing your electronic and social media footprint.
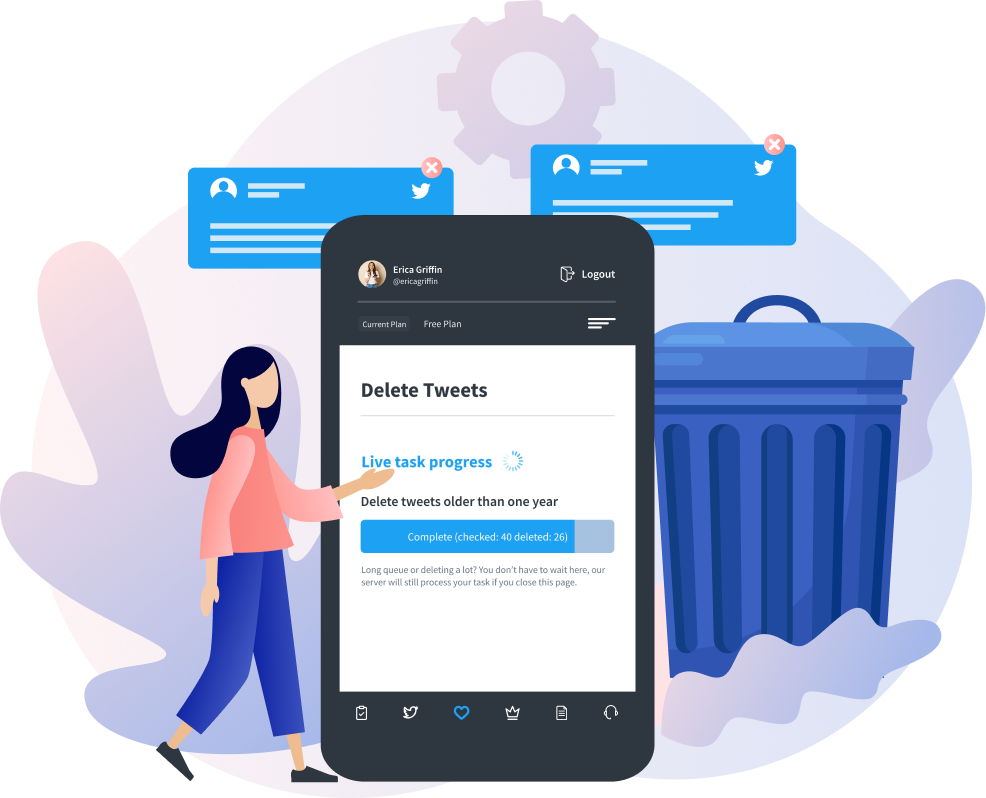
TweetEraser can help you bulk delete tweets to remove them from X and other search engines. A single click can help you import your tweets and Likes into your X archive. TweetEraser is easy to use and designed with a simple algorithm that ensures your account security. With this tool, you needn’t worry about ads while keeping your timeline ever-attractive. So, start filtering and cleaning your Twitter timeline today!